
Federal agency .gov domains have less than three months left to come into compliance with binding operational directive (BOD) 18-01, issued by the Department of Homeland Security (DHS) last October, which requires the use of Domain-based Message Authentication, Reporting and Conformance (DMARC). A DHS representative on Wednesday said that progress in implementing DMARC has been strong, but that initial implementation is far from the finish line.
DMARC is an email authentication protocol that verifies the authenticity of an email’s sender in order to prevent spoofing and phishing. These email exploits remain some of the most common attack vectors used by hackers targeting Federal systems, prompting the DHS BOD requiring agencies to adopt the protocol.
“We’re ultimately working towards raising the government’s security posture, to protect information, to reduce risks based on the common attack vectors that we see through phishing and really ensure first and foremost that the American public can trust the services and communications that it receives from the United States government,” Michael Duffy, branch chief for the Office of Cybersecurity and Communications at DHS, said Wednesday during a webinar hosted by Federal Computer Week.
We learned in June that Federal agencies are leading other security-conscious sectors like tech and banking in DMARC adoption, according to research from Valimail. Duffy brought fresh figures to back up that claim.
Since the BOD was released last October, DMARC adoption on Federal .gov domains has risen from 20 percent to 87 percent, Duffy said. He called the BOD “one of the most ambitious and bold to date” but also praised government-wide acceptance.
“We’re seeing really great progress across individual agencies and observed really fantastic collaboration between DHS and the larger Federal community as we work towards a common goal,” he said.
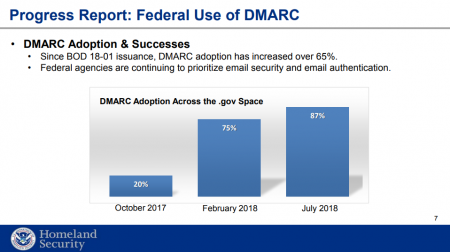
But an 87 percent adoption rate doesn’t tell the whole story. Noting that true DMARC implementation is “very complicated,” Duffy explained that the BOD instructs agencies to set their DMARC policies to “reject” by October 16, 2018. Federal .gov domains with active enforcement are far fewer than 87 percent. Valimail said last month that both Federal agencies and contractors were still not using DMARC policies to actively protect email.
At the time the BOD was released, what about those 20 percent of .gov domains that had already adopted DMARC? Only about 20 percent of those had properly enforced DMARC policies, meaning just 4 percent – 51 of 1,315 Federal government domains – were fully protected by DMARC, according to Valimail. The research did find that protected Federal domains has risen to about 31 percent by June, a sign that progress is on the way.
Steve Whittle, head of Customer Success at Valimail, said Wednesday at the webinar that achieving enforcement is a three-step process. First is the monitoring phase, which involves the initial implementation of a DMARC record, to see where email is originating and getting a first sense of potential fraudulent activity. The great majority of Federal domains have adopted and reached this point.
The second phase involves configuring DMARC policies, which Whittle said many government agencies currently find themselves in. This phase involves determining the email senders and services for which delivery is permitted.
The third phase is continuous enforcement, where the configured policies are put into active use, all senders are properly authenticated, and any unauthorized use of email is blocked. This is the DHS goal of a “reject” policy, and where the majority of .gov domains still haven’t arrived.
With the October 16 date looming, the DMARC adoption uptick needs to translate to active enforcement and “reject” policies if agencies are to comply with the BOD, Duffy said. From a knowledge perspective, it will require investment from the IT department. Duffy said that assembling a team that works to understand agency email architecture and the associated assets and inventory “are critical to getting started.”
