In a virtually unnoticed message to Congress this month, President Donald Trump outlined his new guiding principles for reforming the Selective Service process, as called for by the 2017 National Defense Authorization Act. And the Trump approach calls for a renewed focus on “critical skills.” […]
The government doesn’t need “nongovernment culture” to improve cybersecurity. What it needs is to recruit a workforce with a long-term vision of service and innovators driven not by the prospect of living a life of success but of living a life of meaning. Nowhere is this more apparent than at NASA. […]
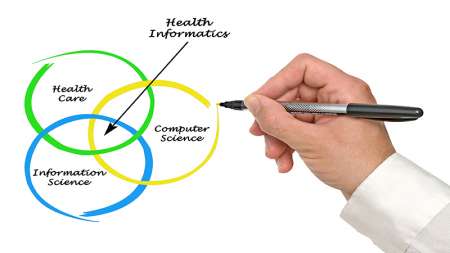
A truly stunning detail overlooked by most observers during the confirmation process of David Shulkin to become secretary of Veterans Affairs is that the VA is going to hire a chief health informatics officer to lead the agency’s electronic health record strategy. […]
The organizational changes flowing around in James Comey’s head aren’t new or revolutionary. But they are for the FBI, and they could fundamentally alter what it means to be an FBI agent. […]
The Marine Corps has a problem, and it isn’t about social media, how long it will take male Marines to accept women in the ranks, or how Marines “treat each other” off the battlefield. […]
There are strong signals that President Donald Trump’s executive order on cybersecurity may still be weeks, if not months, away from hitting the street in final form. After leaking two draft versions in rapid succession, the White House finds itself struggling to define the metrics it will use to hold agency leaders accountable. […]
Since the news broke that WikiLeaks published thousands of documents detailing the CIA’s hacking arsenal targeting iPhones, driverless cars, and smart TVs, has anybody wondered why the CIA would focus on iPhones and Samsung Smart TVs? […]
Our Middle East listening posts indicate that the same drones many of us are buying on Amazon.com and flying around local parks are now being outfitted with improvised explosive devices and other weapons by the Islamic State and other terrorist groups. […]
A new bill would require Federal agencies to obtain a search warrant to access information on citizens without their knowledge. It comes in response to the increasing use of “stingray” devices that Federal, state, and local agencies use to track criminal suspects, capturing data on innocent bystanders as well. […]
President Donald Trump was supposed to sign a sweeping cybersecurity executive order last month, but delayed its release shortly after meeting with senior national security leaders and industry experts. But the timing of the final order is far less important than the changes that are likely being made to the content of the order. […]
Cloud computing has become virtually synonymous with IT modernization throughout the Federal government. But the government’s cloud record has been anything but consistent and predictable, making the effort to measure progress and plan for IT modernization efforts called for by Congress and the Trump administration nearly impossible. […]
President Donald Trump’s Federal hiring freeze on all non-military and public safety positions met with almost immediate condemnation from Federal employee unions. But analysts worry about the impact the freeze could have on the ability of agencies to bring in new technology talent. […]
Outgoing Undersecretary of Defense for Acquisition, Technology and Logistics Frank Kendall during his final public appearance said the only measurement that really counts in DoD acquisitions is if the things the Pentagon buys increase the combat capabilities of the military. […]
What’s really behind President-elect Donald Trump’s very public rebuke of national intelligence agencies? It has very little to do with the intelligence collected on Russian hacking activities. What Americans are watching play out 140 characters at a time is a distasteful game of political retribution orchestrated by Trump’s pick for national security adviser, retired Army Gen. Michael Flynn. […]
There’s a new CTO at the National Archives and Records Administration….Inspector general may be out at NSA….And ransomware targets industrial systems. […]
Who will be leaving the Federal CIO ranks during the transition and who might be staying? With the help of a veteran industry executive who has tracked this very issue, we pulled together a list of 25 Federal CIOs. […]
The technological stars may be aligning for health IT giant Cerner. And that could mean another multibillion-dollar government contract–this time with the Department of Veterans Affairs. […]
Analysts and pundits have been wringing their hands for the past two weeks trying to predict what the election of Donald Trump means for Federal IT and technology policy. Of course, nobody has a good answer because nobody really knows. […]
What do you get when you cross a third-generation Portuguese congressman with a completely logical plan to consolidate the military’s Joint Intelligence Analysis Centers around the world? […]
Changes could be coming to the FITARA scorecard….How does the president-elect’s stated distrust of the intelligence community affect IC Information Technology Enterprise?…And 18F’s project at the Centers For Medicare & Medicaid Services stirs interest. […]
Is Federal IT’s old guard really ready to pass the banner to the millennial generation? […]
One veteran Federal analyst tells The Situation Report that the “average” presidential transition ushers in 5,000 new appointments, 1,000 of which require Senate confirmation. But the upcoming transition promises to be a unique experience, regardless of who gets elected. […]
News broke this week that the FBI in August had arrested another NSA employee for allegedly stealing and hoarding highly classified information in his home and car. Like Edward Snowden, the employee worked for Federal contractor Booz Allen Hamilton, raising questions about the efficacy of the security reforms put in place at the agency. […]
Is the Obama administration’s election year lust for Silicon Valley’s dead presidents destroying the future of the career Federal technology leader?…The pace of the Department of Homeland Security’s Continuous Diagnostics and Mitigation program is frustrating to some….And a near-miss for Snowden? […]
The Secret Service has an interesting class photo….The CIA is taking cues from the advertising technology industry….IARPA is investing in research into homomorphic encryption—a potential game-changer in the worlds of privacy and security that enables encrypted queries of encrypted databases….And synthetic biology is keeping Jason Matheny up at night. […]
The storm clearly has not passed for some big programs run by the General Services Administration, including FedRAMP’s spending of $150,000 in taxpayer money to duplicate an online dashboard capability that had already been developed in the private sector and made available to the government for free….Also, Rep. Will Hurd, R-Texas, is back with another bill aimed at IT modernization. […]
The Situation Report has the benefit of an intelligence collection network that is reporting some interesting twists and turns in the White House’s finally completed search for the government’s first Federal CISO. […]
“There is no such thing as absolute privacy in America.” That’s what FBI Director James Comey said in a counterattack on Silicon Valley’s stance on encryption. […]
The Pentagon’s latest buzz phrase is Identity Activities, which means the Pentagon wants to employ data analysis tools that will leverage biographical, biological, behavioral, and reputational data inputs to help the military determine the identity of a person they encounter on the battlefield and whether that person poses a threat. […]
Major changes in the cyber threat landscape during the last few years have forced the NSA to embrace a new reorganization strategy that officials argue is urgently needed to defend the nation from an onslaught of state-sponsored hacking attacks. […]
Archives
- April 2017 (3)
- March 2017 (4)
- February 2017 (4)
- January 2017 (3)
- December 2016 (3)
- November 2016 (3)
- October 2016 (3)
- September 2016 (4)
- August 2016 (5)
- July 2016 (4)
- June 2016 (4)
- May 2016 (4)
- April 2016 (4)
- March 2016 (5)
- February 2016 (4)
- January 2016 (4)
- December 2015 (3)