MeriTalk recently connected with Jim Smid, chief technology officer at Iron Bow Technologies, to discuss hyper converged infrastructure (HCI) and how it can jump-start modernization. Iron Bow is a solutions integrator that helps companies and organizations implement new technologies, integrate those technologies, and create system efficiencies.

MeriTalk: What are the advantages of leveraging HCI to jump-start modernization and cloud migration?
Jim Smid: It’s all about simplification. Not only is the technology streamlined, but HCI is also easier to use from an operator and manager perspective. With HCI, users can advance toward the goal of commoditizing the use of their hardware–giving them greater flexibility in what that hardware is capable of doing.
HCI is an excellent step toward a software-defined data center (SDDC), which enables agencies to boost the utilization and flexibility of their hardware and make decisions based on how they need to use that hardware at any given moment. HCI plays an important role in orchestrating and automating these processes so organizations can get the full benefit of their hardware spend.
When it comes to jump-starting cloud migration, if the infrastructure isn’t simple and efficient, it’s not going to work. To move to cloud, organizations must drive efficiencies. HCI is a great way to simplify how you drive efficiencies and how to make cloud infrastructure work.
MeriTalk: Which of these advantages matters most to agencies today?
J.S.: Simplicity is most important to agencies. The ability to quickly deploy applications on HCI makes the agency much more efficient. This is especially important as agencies’ IT requirements grow and the shortage of skilled IT professionals persists. HCI can play an important role in helping agencies optimize the impact of their IT spend and resources.
MeriTalk: How else does a HCI approach help remove barriers to modernization and improve performance?
J.S.: The HCI approach has been around for a while, but there are several technology changes–such as flash storage and recovery management technologies–that help remove the barriers to modernization and improve performance across applications. HCI enables organizations to scale very simply, and gives them flexibility to leverage their overall infrastructure to drive greater efficiency.
MeriTalk: In what types of environments are you seeing the greatest traction for this approach?
J.S.: The greatest traction for a HCI approach is in virtual desktop infrastructures. However, as technical advances mature, we are starting to see HCI used as a more generic landing place for all kinds of applications. People are beginning to look to HCI before building something out in a traditional converged or reference architecture, and it is becoming a more realistic alternative for a wider range of applications.
MeriTalk: What myths or misconceptions are most common when talking to customers about deploying HCI?
J.S.: The myth is around performance. And it’s truly a myth today. With new technology, such as flash, the ability to extend memory, as well as various storage advances, people are realizing what HCI can do. We are trying to get people past the perception that HCI won’t scale and we’re now seeing greater acceptance. Once our customers use HCI for more than what they originally bought it for, the approach continues to sell itself.
MeriTalk: Can you share a few best practices for the journey to HCI?
J.S.: The No. 1 best practice is to work with someone who has been there before and is familiar with the latest HCI advances. Agencies should lean on a partner with experience in how to design the infrastructure–one who understands the various iterations and offerings in the marketplace and how HCI can fit into their existing infrastructure. To ensure success, organizations must rely on subject matter experts, like Iron Bow.
MeriTalk: What do you think the administration change will mean for IT modernization initiatives, including the Data Center Optimization Initiative?
J.S.: That remains to be seen. I think the new administration has talked about driving efficiencies and investing in the Department of Defense, so I’m cautiously optimistic there will be a push toward modernization in IT and the benefits that modernization gives the military and government.


 Despite new policies designed to give chief information officers more spending power, some Federal CIOs don’t see any improvement in acquiring the technology they need to keep their systems secure. Luke McCormack, CIO of the Department of Homeland Security, said that whether or not MGT passes the Senate, systems will remain unfunded. Despite this, claims that the fund will cost about $9 billion prevent an agreement
Despite new policies designed to give chief information officers more spending power, some Federal CIOs don’t see any improvement in acquiring the technology they need to keep their systems secure. Luke McCormack, CIO of the Department of Homeland Security, said that whether or not MGT passes the Senate, systems will remain unfunded. Despite this, claims that the fund will cost about $9 billion prevent an agreement  The Department of Veterans Affairs this week launched a new website to raise awareness of the agency’s Digital Health Platform–a cloud-based approach to integrating veterans health data to produce what the agency calls real-time, analytics-driven, personalized care. VA’s current EHR, known as VistA, is a 40-year-old system that the agency continues to modernize while it debates a potential commercial replacement. According to the new website, “DHP provides a comprehensive dashboard spanning a veteran’s
The Department of Veterans Affairs this week launched a new website to raise awareness of the agency’s Digital Health Platform–a cloud-based approach to integrating veterans health data to produce what the agency calls real-time, analytics-driven, personalized care. VA’s current EHR, known as VistA, is a 40-year-old system that the agency continues to modernize while it debates a potential commercial replacement. According to the new website, “DHP provides a comprehensive dashboard spanning a veteran’s  The third and most recent FITARA scorecard was released Dec. 6. DOT, which has received overall D’s on the previous two scorecards, received an F+ this time around. A spokesperson said that the report card does not reflect the
The third and most recent FITARA scorecard was released Dec. 6. DOT, which has received overall D’s on the previous two scorecards, received an F+ this time around. A spokesperson said that the report card does not reflect the  A majority of the 24 major agencies defined under the CFO Act are expected to meet the deadline to begin reporting their spending information. Under the Digital Accountability and Transparency Act of 2014 (DATA Act), Federal agencies are required to begin reporting their spending information to the Department of the Treasury and the Office of Management and
A majority of the 24 major agencies defined under the CFO Act are expected to meet the deadline to begin reporting their spending information. Under the Digital Accountability and Transparency Act of 2014 (DATA Act), Federal agencies are required to begin reporting their spending information to the Department of the Treasury and the Office of Management and  Incumbent: Gundeep Ahluwalia
Incumbent: Gundeep Ahluwalia Incumbent: Jonathan Alboum
Incumbent: Jonathan Alboum
 Incumbent: Sonny Bhagowalia
Incumbent: Sonny Bhagowalia Incumbent: Sylvia Burns
Incumbent: Sylvia Burns Police departments across the country that received Federal grants for body worn cameras are concerned about sharing information with the agencies responsible for this funding. Some police departments have gone so far to as to say they would not share body camera footage unless Federal agencies compelled them. Body cameras that are turned on all the time can be a double-edged sword. While these constantly running devices could potentially improve officer accountability in certain cases, there are also situations in which this content
Police departments across the country that received Federal grants for body worn cameras are concerned about sharing information with the agencies responsible for this funding. Some police departments have gone so far to as to say they would not share body camera footage unless Federal agencies compelled them. Body cameras that are turned on all the time can be a double-edged sword. While these constantly running devices could potentially improve officer accountability in certain cases, there are also situations in which this content  An effort led by Sen. Ron Wyden, D-Ore., to block or delay changes to Rule 41 of the Federal Rules of Criminal Procedure failed to pass the Senate floor on Wednesday, causing the changes to the rule to go into effect at midnight on Dec. 1. The changes will allow law enforcement to obtain warrants to search computers in an unknown location and to search any device that the hacker has broken into, potentially granting access to multiple privately owned computers with one warrant. The ACLU is disappointed that Congress did not halt
An effort led by Sen. Ron Wyden, D-Ore., to block or delay changes to Rule 41 of the Federal Rules of Criminal Procedure failed to pass the Senate floor on Wednesday, causing the changes to the rule to go into effect at midnight on Dec. 1. The changes will allow law enforcement to obtain warrants to search computers in an unknown location and to search any device that the hacker has broken into, potentially granting access to multiple privately owned computers with one warrant. The ACLU is disappointed that Congress did not halt 
 IBM suggested a new model of education, which includes six years of high school, in a letter to President-elect Donald Trump from Nov. 15. Ginni Rometty, chief executive officer of IBM, said that there will soon be 100 schools that follow this method across the country. After their third year, they’re eligible to take at least
IBM suggested a new model of education, which includes six years of high school, in a letter to President-elect Donald Trump from Nov. 15. Ginni Rometty, chief executive officer of IBM, said that there will soon be 100 schools that follow this method across the country. After their third year, they’re eligible to take at least 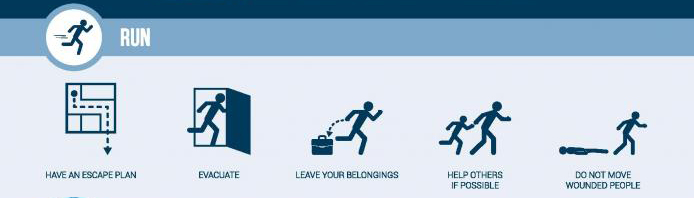
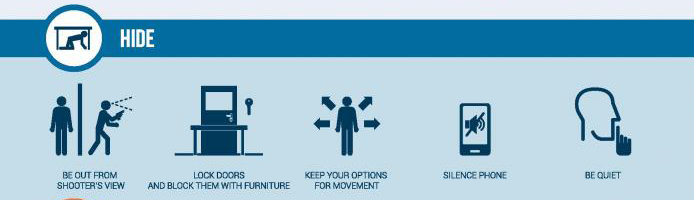

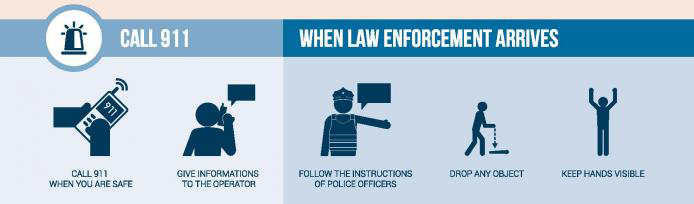
 President-elect Donald Trump during his transition is relying on two American Enterprise Institute contributors for advice on technology policy, which consists of calls for deregulation of the National Security Agency and an end to net neutrality: Jeffrey Eisenach and Mark Jamison. Eisenach said the government should create a Federal Cybersecurity Service, a civilian agency with the NSA’s cyber defense assets and the powers of the military and law enforcement to react to cybersecurity problems without having to go through the obstacles of gaining permission from other levels of government. In Trump’s YouTube video, which outlines his plans for his first 100 days in office, he said he would allow the military to develop and use offensive cyber capabilities; however, that poses a problem for the protection of private companies that have been the
President-elect Donald Trump during his transition is relying on two American Enterprise Institute contributors for advice on technology policy, which consists of calls for deregulation of the National Security Agency and an end to net neutrality: Jeffrey Eisenach and Mark Jamison. Eisenach said the government should create a Federal Cybersecurity Service, a civilian agency with the NSA’s cyber defense assets and the powers of the military and law enforcement to react to cybersecurity problems without having to go through the obstacles of gaining permission from other levels of government. In Trump’s YouTube video, which outlines his plans for his first 100 days in office, he said he would allow the military to develop and use offensive cyber capabilities; however, that poses a problem for the protection of private companies that have been the  Rep. Gerry Connolly, D-Va., spearheaded a letter signed by 15 members of the House Foreign Affairs Committee to request that the committee hold a hearing on the attempts by foreign powers to influence the U.S. presidential election. “It is our hope that a potential hearing would address what interference took place, how it happened, and how we can prevent such actions going forward, in order to preserve the integrity of the U.S. electoral process,” Connolly told MeriTalk. “Electronic security is an important aspect, but not the only potential form of foreign interference in U.S. elections.” “Ranking Member (Eliot) Engel, one of our most cherished institutions, democratic elections free of foreign interference, is in question,”
Rep. Gerry Connolly, D-Va., spearheaded a letter signed by 15 members of the House Foreign Affairs Committee to request that the committee hold a hearing on the attempts by foreign powers to influence the U.S. presidential election. “It is our hope that a potential hearing would address what interference took place, how it happened, and how we can prevent such actions going forward, in order to preserve the integrity of the U.S. electoral process,” Connolly told MeriTalk. “Electronic security is an important aspect, but not the only potential form of foreign interference in U.S. elections.” “Ranking Member (Eliot) Engel, one of our most cherished institutions, democratic elections free of foreign interference, is in question,”  Leaders of the University at Albany, State University of New York’s cybersecurity program are working on internship opportunities with companies in the area for students to gain cybersecurity experience. The program divided $1 million in grant funding evenly among five academic institutions to support cybersecurity education among students. Between 250 and 300 students are enrolled in UAlbany’s cybersecurity program, which includes a master’s track, as well as accounting and
Leaders of the University at Albany, State University of New York’s cybersecurity program are working on internship opportunities with companies in the area for students to gain cybersecurity experience. The program divided $1 million in grant funding evenly among five academic institutions to support cybersecurity education among students. Between 250 and 300 students are enrolled in UAlbany’s cybersecurity program, which includes a master’s track, as well as accounting and  The Department of Education has plans to build a Federal database of student information, which has sparked protest from privacy groups. The Federal unit records system would include information on student performance throughout school and track students into their careers. Supporters said that the database will help inform policy decisions and enable students to make better choices when it comes to higher
The Department of Education has plans to build a Federal database of student information, which has sparked protest from privacy groups. The Federal unit records system would include information on student performance throughout school and track students into their careers. Supporters said that the database will help inform policy decisions and enable students to make better choices when it comes to higher  President-elect Donald Trump ran his campaign on the commitment to remove illegal Mexican residents and temporarily ban Muslims from entering the country. Extreme vetting policies would logically accompany these stringent immigration goals. “We need to avoid data glut and information overload,” said
President-elect Donald Trump ran his campaign on the commitment to remove illegal Mexican residents and temporarily ban Muslims from entering the country. Extreme vetting policies would logically accompany these stringent immigration goals. “We need to avoid data glut and information overload,” said  “What we need to start thinking about now is not how we defend against a President-elect Trump, but how we defend the rights of everyone everywhere,” according to Edward Snowden, the National Security Agency contractor responsible for leaking information about the U.S. government’s mass surveillance program in 2013. Snowden said the Internet is a tool that was built to empower people, but too often it is used by authoritarian governments to disempower dissenters. To overcome this problem, Snowden said that technology companies need to ensure every communication system is “protected by default” from end to end
“What we need to start thinking about now is not how we defend against a President-elect Trump, but how we defend the rights of everyone everywhere,” according to Edward Snowden, the National Security Agency contractor responsible for leaking information about the U.S. government’s mass surveillance program in 2013. Snowden said the Internet is a tool that was built to empower people, but too often it is used by authoritarian governments to disempower dissenters. To overcome this problem, Snowden said that technology companies need to ensure every communication system is “protected by default” from end to end  In the “Wild West” of augmented reality applications, the U.S. government has to balance the concerns of helping to protect consumer privacy and security while also leaving room for companies to freely innovate, according to witnesses at a Senate Energy and Commerce hearing. It doesn’t always feel like there’s a sheriff out there to help out,” said John Hanke of Niantic. On the other side of the spectrum, white hat hackers, whose aim is to discover vulnerabilities in AR software and help companies patch them, worry that they will be prosecuted for their work. “We worry that our reverse engineering or our attempts to figure out what the flaws might be with a device will be met with legal
In the “Wild West” of augmented reality applications, the U.S. government has to balance the concerns of helping to protect consumer privacy and security while also leaving room for companies to freely innovate, according to witnesses at a Senate Energy and Commerce hearing. It doesn’t always feel like there’s a sheriff out there to help out,” said John Hanke of Niantic. On the other side of the spectrum, white hat hackers, whose aim is to discover vulnerabilities in AR software and help companies patch them, worry that they will be prosecuted for their work. “We worry that our reverse engineering or our attempts to figure out what the flaws might be with a device will be met with legal  Agency Twitter use has become an important factor in communication between the Federal community and the public. Agencies that have the best Twitter strategy, such as the State Department, tend to have been present on Twitter for the longest and have picked up the most followers. MeriTalk studied the Twitter accounts of 15 agencies to determine number of followers, number of tweets, and year that the Twitter accounts were created to determine which agencies are the most successful on the
Agency Twitter use has become an important factor in communication between the Federal community and the public. Agencies that have the best Twitter strategy, such as the State Department, tend to have been present on Twitter for the longest and have picked up the most followers. MeriTalk studied the Twitter accounts of 15 agencies to determine number of followers, number of tweets, and year that the Twitter accounts were created to determine which agencies are the most successful on the 

 The incoming Trump administration plans to get rid of 18F, the digital services team located within the General Services Administration that has been criticized recently for its spending practices, according to a senior administration official. “People that have actual IT experience will be put into positions,” said the official, who spoke to MeriTalk on condition of anonymity because of the sensitive nature of the transition discussions. Republican Donald Trump won the presidential election on Nov. 8, raising questions about what lies ahead
The incoming Trump administration plans to get rid of 18F, the digital services team located within the General Services Administration that has been criticized recently for its spending practices, according to a senior administration official. “People that have actual IT experience will be put into positions,” said the official, who spoke to MeriTalk on condition of anonymity because of the sensitive nature of the transition discussions. Republican Donald Trump won the presidential election on Nov. 8, raising questions about what lies ahead  Farmers should save their cows’ numbers in their phones because cows can now send farmers a text message when they’re feeling under the weather. The farmer maintains a base station that reads all of the data from each of the cows, adds the real-time data to the outdoor temperature and humidity, and then uploads it to the cloud. The system can also email a veterinarian to make an appointment for the farmer, to ensure the cow’s illness can
Farmers should save their cows’ numbers in their phones because cows can now send farmers a text message when they’re feeling under the weather. The farmer maintains a base station that reads all of the data from each of the cows, adds the real-time data to the outdoor temperature and humidity, and then uploads it to the cloud. The system can also email a veterinarian to make an appointment for the farmer, to ensure the cow’s illness can  The Internet of Things (IoT) is a great tool for those with disabilities, experts say, but government and industry can do more to ensure that IoT devices are accessible by all, through the implementation of universal design. “The Internet of Things offers opportunities to increase independence by reducing the need for personal assistance at home,” said Daniel Castro, vice president at the Information Technology and Innovation Foundation, adding that smart pill bottles, sensors in the home, and advances in assistance robots would enable people with disabilities to live at home or alone while still ensuring quality care. “These technologies have potentially enormous benefits for people with disabilities, but these benefits are by
The Internet of Things (IoT) is a great tool for those with disabilities, experts say, but government and industry can do more to ensure that IoT devices are accessible by all, through the implementation of universal design. “The Internet of Things offers opportunities to increase independence by reducing the need for personal assistance at home,” said Daniel Castro, vice president at the Information Technology and Innovation Foundation, adding that smart pill bottles, sensors in the home, and advances in assistance robots would enable people with disabilities to live at home or alone while still ensuring quality care. “These technologies have potentially enormous benefits for people with disabilities, but these benefits are by  The General Services Administration will start a council of agency Web and digital directors by Dec. 8, according to a
The General Services Administration will start a council of agency Web and digital directors by Dec. 8, according to a 

 The National Institute of Standards and Technology announced the release of CyberSeek, an interactive map that shows cybersecurity job availability by both state and locality. At the time of publication, the map showed nearly 349,000 cybersecurity job openings nationwide and a total employed cybersecurity workforce of more than 778,000. The website also includes a Career Pathway section, which provides job seekers and those looking to get into cybersecurity careers with entry-level positions, salary statistics, and potential career pathways. The tool is also designed to help employers find areas of the country with a high saturation of cybersecurity workers, as the current market has more open positions than workers
The National Institute of Standards and Technology announced the release of CyberSeek, an interactive map that shows cybersecurity job availability by both state and locality. At the time of publication, the map showed nearly 349,000 cybersecurity job openings nationwide and a total employed cybersecurity workforce of more than 778,000. The website also includes a Career Pathway section, which provides job seekers and those looking to get into cybersecurity careers with entry-level positions, salary statistics, and potential career pathways. The tool is also designed to help employers find areas of the country with a high saturation of cybersecurity workers, as the current market has more open positions than workers  MeriTalk conducted a Q&A with Filippo Menczer, a professor of Informatics and Computer Science and the director of the Center for Complex Networks and Systems Research at the Indiana University School of Informatics and Computing. In May 2016, he and his team launched the Observatory on Social Media (OSoMe), a big data hub for people to analyze
MeriTalk conducted a Q&A with Filippo Menczer, a professor of Informatics and Computer Science and the director of the Center for Complex Networks and Systems Research at the Indiana University School of Informatics and Computing. In May 2016, he and his team launched the Observatory on Social Media (OSoMe), a big data hub for people to analyze  Censeo Consulting Group worked with Cyrrus Analytics and Hettinger Strategy Group to create the report “FITARA at a Crossroads.” MeriTalk summarizes the 10 recommendations. GAO would continue to audit the government’s ability to meet legislative requirements. If GAO could access OMB’s agency data, which is more detailed than the information stored by any other entity, they would be able to make more accurate assessments. The grading criteria need to reflect new fields and provide incentive for
Censeo Consulting Group worked with Cyrrus Analytics and Hettinger Strategy Group to create the report “FITARA at a Crossroads.” MeriTalk summarizes the 10 recommendations. GAO would continue to audit the government’s ability to meet legislative requirements. If GAO could access OMB’s agency data, which is more detailed than the information stored by any other entity, they would be able to make more accurate assessments. The grading criteria need to reflect new fields and provide incentive for  The General Services Administration’s digital services organization, known as 18F, has consistently overestimated revenue projections by tens of millions of dollars, allowed IT staff to spend more than half of their time on non-billable projects, and continued to hire employees at the top of the Federal pay scale despite losses that now amount to more than $31 million, a new inspector general report found. The report found that 18F overestimated revenues for each year since its founding in 2014. Despite these revenue discrepancies, 18F continued to hire new staff from Silicon Valley. The report also found that “less than half of staff time was spent working on projects billed to Federal agencies.” The remaining time was spent promoting 18F projects, developing 18F brand, and developing
The General Services Administration’s digital services organization, known as 18F, has consistently overestimated revenue projections by tens of millions of dollars, allowed IT staff to spend more than half of their time on non-billable projects, and continued to hire employees at the top of the Federal pay scale despite losses that now amount to more than $31 million, a new inspector general report found. The report found that 18F overestimated revenues for each year since its founding in 2014. Despite these revenue discrepancies, 18F continued to hire new staff from Silicon Valley. The report also found that “less than half of staff time was spent working on projects billed to Federal agencies.” The remaining time was spent promoting 18F projects, developing 18F brand, and developing  The Department of State has moved from leased data center facilities to data centers on government property by using a modular approach. Two years ago, the State Department mandated that the agency start to use government-owned property data centers. The agency moved from using an 11,000-square-foot lease facility to an 800-square-foot
The Department of State has moved from leased data center facilities to data centers on government property by using a modular approach. Two years ago, the State Department mandated that the agency start to use government-owned property data centers. The agency moved from using an 11,000-square-foot lease facility to an 800-square-foot  When Tony Summerlin, senior strategic adviser at the Federal Communications Commission helped write the first Federal Risk and Authorization Management Program, he said he envisioned the program as a much quicker and sleeker version of what it is today. Summerlin, who spoke at a panel at ServiceNow’s Now Forum on Oct. 26, said his goal was to draft a plan that would accelerate people to the cloud. Instead, it turned into a 1,500-page bureaucratic exercise that he said “wasn’t the point” of the document. According to Summerlin, speed is one of the biggest challenges to Federal initiatives across the board, not just in the
When Tony Summerlin, senior strategic adviser at the Federal Communications Commission helped write the first Federal Risk and Authorization Management Program, he said he envisioned the program as a much quicker and sleeker version of what it is today. Summerlin, who spoke at a panel at ServiceNow’s Now Forum on Oct. 26, said his goal was to draft a plan that would accelerate people to the cloud. Instead, it turned into a 1,500-page bureaucratic exercise that he said “wasn’t the point” of the document. According to Summerlin, speed is one of the biggest challenges to Federal initiatives across the board, not just in the  The Department of Justice plans to have three physical data centers by 2019, according to Mark Busby, program manager of data center transformation for DOJ. Busby said that he and his team are still working to optimize data centers and shared services, as well as manage colocation facilities. Colocation facilities offer space, power, heating, and cooling for agencies seeking to store hardware. “The less I get to put into physical data
The Department of Justice plans to have three physical data centers by 2019, according to Mark Busby, program manager of data center transformation for DOJ. Busby said that he and his team are still working to optimize data centers and shared services, as well as manage colocation facilities. Colocation facilities offer space, power, heating, and cooling for agencies seeking to store hardware. “The less I get to put into physical data 
 The U.S. government is charging Harold T. Martin III under the Espionage Act after concluding that the National Security Agency contractor took home 50 terabytes of classified data, which was first reported by the Washington Post. Martin also had the cyber weapons that the hacker group the Shadow Brokers were attempting to sell online, although prosecutors can’t find the link between Martin and the group. It doesn’t appear that Martin’s computer was breached. Martin also took six banker’s boxes full of documents, which he stored openly in his
The U.S. government is charging Harold T. Martin III under the Espionage Act after concluding that the National Security Agency contractor took home 50 terabytes of classified data, which was first reported by the Washington Post. Martin also had the cyber weapons that the hacker group the Shadow Brokers were attempting to sell online, although prosecutors can’t find the link between Martin and the group. It doesn’t appear that Martin’s computer was breached. Martin also took six banker’s boxes full of documents, which he stored openly in his  Educational technology has demonstrated numerous benefits for both educators and students; however, recent advancements are not without concerns. As ed tech becomes more prevalent in the classroom, privacy rights activists and the Federal government are growing concerned about how sensitive student data is being handled and secured. The Center for Democracy & Technology, along with the law firm BakerHostetler, developed a state-by-state compendium of privacy laws relating to the collection, use, and sharing
Educational technology has demonstrated numerous benefits for both educators and students; however, recent advancements are not without concerns. As ed tech becomes more prevalent in the classroom, privacy rights activists and the Federal government are growing concerned about how sensitive student data is being handled and secured. The Center for Democracy & Technology, along with the law firm BakerHostetler, developed a state-by-state compendium of privacy laws relating to the collection, use, and sharing  Current international laws surrounding warfare can be applicable to instances of cyber war, according to experts. However, concerns of attribution and automation can complicate the degree of response a nation is legally allowed to take. Michael Schmitt, chairman of the Stockton Center for the Study of International Law at the United States Naval War College and professor of public international law at the University of Exeter, focused on what a nation-state could legally do in the event of a cyberattack by another country or
Current international laws surrounding warfare can be applicable to instances of cyber war, according to experts. However, concerns of attribution and automation can complicate the degree of response a nation is legally allowed to take. Michael Schmitt, chairman of the Stockton Center for the Study of International Law at the United States Naval War College and professor of public international law at the University of Exeter, focused on what a nation-state could legally do in the event of a cyberattack by another country or  By 2018, students at Northwestern University will not carry metal room keys. The university is in the process of updating student identification cards to grant access to dorm rooms. The majority of students at Northwestern swipe their identification cards, or Wildcards, to access the library, the dining hall, the recreation center, and their dorm buildings; they use conventional keys to get into
By 2018, students at Northwestern University will not carry metal room keys. The university is in the process of updating student identification cards to grant access to dorm rooms. The majority of students at Northwestern swipe their identification cards, or Wildcards, to access the library, the dining hall, the recreation center, and their dorm buildings; they use conventional keys to get into 
 Federal Communications Commission CIO David Bray, who’s been an outspoken proponent of creating so-called #ChangeAgents at every level of an agency’s organizational structure, is bringing his unique brand of thinking to this year’s Executive Leadership Conference (ELC), an annual event hosted by the American Council for Technology-Industry Advisory Council (ACT-IAC) that brings 800 government and industry executives together for two and a half days of leadership development and collaboration. In an extensive interview following the IT Boardwalk session, Bray outlined his plans for
Federal Communications Commission CIO David Bray, who’s been an outspoken proponent of creating so-called #ChangeAgents at every level of an agency’s organizational structure, is bringing his unique brand of thinking to this year’s Executive Leadership Conference (ELC), an annual event hosted by the American Council for Technology-Industry Advisory Council (ACT-IAC) that brings 800 government and industry executives together for two and a half days of leadership development and collaboration. In an extensive interview following the IT Boardwalk session, Bray outlined his plans for  In order to settle on Mars, robots and humans have to work hand in hand, which will be possible soon, according to Red Whittaker, professor at the Robotics Institute at Carnegie Mellon University. “The robotics that support human life on Mars will be an entirely new class of robots,” Whittaker said. “There’s a clear sense of what’s called for and we’re going to come through.” The robots that are on Mars for exploration purposes will have to be updated in order to perceive, plan, and process to solve problems in space. “They have to be compatible with humans,”
In order to settle on Mars, robots and humans have to work hand in hand, which will be possible soon, according to Red Whittaker, professor at the Robotics Institute at Carnegie Mellon University. “The robotics that support human life on Mars will be an entirely new class of robots,” Whittaker said. “There’s a clear sense of what’s called for and we’re going to come through.” The robots that are on Mars for exploration purposes will have to be updated in order to perceive, plan, and process to solve problems in space. “They have to be compatible with humans,”  Gregory Touhill is optimistic about his ability to remain in his position through the presidential transition and has many plans that he hopes to carry through that transition. “I expect to be here through the transition,” Touhill said. “I want to have a cyber desktop exercise,” Touhill said, explaining that if senior leaders can spend even an hour understanding what to do in the event of a cyberattack, it can improve
Gregory Touhill is optimistic about his ability to remain in his position through the presidential transition and has many plans that he hopes to carry through that transition. “I expect to be here through the transition,” Touhill said. “I want to have a cyber desktop exercise,” Touhill said, explaining that if senior leaders can spend even an hour understanding what to do in the event of a cyberattack, it can improve 