Cybersecurity Goals to Guide Federal Software Spending
 Evolving requirements to greatly improve Federal protection of information technology resources will shape Federal software spending. In fact, Federal cyberprotection goals should be augmented and significantly modified, according to recent studies of the Federal market. The linkage between increased Federal investing in cybersecurity and the requirements for bolstering IT protection are portrayed in two newly released reports.
Evolving requirements to greatly improve Federal protection of information technology resources will shape Federal software spending. In fact, Federal cyberprotection goals should be augmented and significantly modified, according to recent studies of the Federal market. The linkage between increased Federal investing in cybersecurity and the requirements for bolstering IT protection are portrayed in two newly released reports.
U.S. Chief Data Scientist: Entrepreneurs Should do a Tour of Duty in Government
 There’s no question that the U.S. government has collected an incredible amount of data. Whether for things like the Census, housing, agriculture, transportation, or health care, Federal agencies have accumulated data from around the country. In the past seven years, the White House has made efforts to leverage more technology at the Federal level.
There’s no question that the U.S. government has collected an incredible amount of data. Whether for things like the Census, housing, agriculture, transportation, or health care, Federal agencies have accumulated data from around the country. In the past seven years, the White House has made efforts to leverage more technology at the Federal level.
Microsoft’s CEO Explains Why His Company Sued the U.S. Government
 Microsoft surprised the world last month when it filed a lawsuit against the U.S. Department of Justice, alleging that the frequent practice of attaching gag orders to search warrants for customer data violates the U.S. Constitution.
Microsoft surprised the world last month when it filed a lawsuit against the U.S. Department of Justice, alleging that the frequent practice of attaching gag orders to search warrants for customer data violates the U.S. Constitution.
On Monday, CEO Satya Nadella told a group of tech luminaries why the company did so: Microsoft has a strong view on its privacy promises to users, and the company will fight to prevent government overreach that, in its view, compromises the principles of privacy.
Why Open and Frugal Should Be the Default for Government IT
 With public-sector information-technology projects at any level of government, one does not have to look too far to find examples of waste and worse. In the wake of a series of failed projects, Hawaii is auditing its last four years of IT spending. On the local-government level, it would be hard to find a better example of what can go wrong than New York City’s CityTime payroll-system project, abandoned after its costs ballooned from $63 million to $700 million amid mismanagement and outright corruption.
With public-sector information-technology projects at any level of government, one does not have to look too far to find examples of waste and worse. In the wake of a series of failed projects, Hawaii is auditing its last four years of IT spending. On the local-government level, it would be hard to find a better example of what can go wrong than New York City’s CityTime payroll-system project, abandoned after its costs ballooned from $63 million to $700 million amid mismanagement and outright corruption.
Tech Companies are Unlikely to Oppose Government Demands on Data Access
 Can other technology companies defy the government the way Apple did when asked to help U.S. investigators crack the code of iPhone 5C? Unlikely. Especially in jurisdictions where the governments may not be so benign in pursuing hidden material in electronic devices or data centers. Not EMC Corporation, the world’s largest data storage multinational.
Can other technology companies defy the government the way Apple did when asked to help U.S. investigators crack the code of iPhone 5C? Unlikely. Especially in jurisdictions where the governments may not be so benign in pursuing hidden material in electronic devices or data centers. Not EMC Corporation, the world’s largest data storage multinational.


 Under the appendix, Federal agencies are required to subject security controls for major applications and support systems to audits at least every three years. “While some documentation of security controls is essential, these three-year assessments are not cost-effective or consistent with best-practices or other Federal policies,” the lawmakers said. Carper and Johnson requested OMB to submit its response to the Senate
Under the appendix, Federal agencies are required to subject security controls for major applications and support systems to audits at least every three years. “While some documentation of security controls is essential, these three-year assessments are not cost-effective or consistent with best-practices or other Federal policies,” the lawmakers said. Carper and Johnson requested OMB to submit its response to the Senate  U.S. Chief Information Officer Tony Scott Tuesday hinted his office may be working to help guide Federal agencies to adopt “bimodal IT” to balance modern IT with old but necessary systems.
U.S. Chief Information Officer Tony Scott Tuesday hinted his office may be working to help guide Federal agencies to adopt “bimodal IT” to balance modern IT with old but necessary systems. The senators say the lack of a new policy is preventing Federal agencies from moving to automated systems that can better protect Federal networks from cybersecurity threats. The existing Federal cybersecurity policy was created in 2000 and the threat landscape has evolved
The senators say the lack of a new policy is preventing Federal agencies from moving to automated systems that can better protect Federal networks from cybersecurity threats. The existing Federal cybersecurity policy was created in 2000 and the threat landscape has evolved  One of the most recent developments was the formation of a Federal Commission on Enhancing National Cybersecurity. Another was the formal introduction in Congress of the administration’s information technology investment plan, which is heavily tilted toward cybersecurity protection. The goal of the panel is to make recommend actions that can be taken over the next decade to enhance cybersecurity awareness and protections throughout government and the private sector, according to a
One of the most recent developments was the formation of a Federal Commission on Enhancing National Cybersecurity. Another was the formal introduction in Congress of the administration’s information technology investment plan, which is heavily tilted toward cybersecurity protection. The goal of the panel is to make recommend actions that can be taken over the next decade to enhance cybersecurity awareness and protections throughout government and the private sector, according to a  Facebook has published its latest Global Government Requests Report covering the second half of 2015. The transparency report reveals that there has been a 13 percent increase in the number of government requests for data, but it also shows that Facebook is still not able to be as transparent as it might want. For the first time the social network is able to report about the number of data requests that have a non-disclosure
Facebook has published its latest Global Government Requests Report covering the second half of 2015. The transparency report reveals that there has been a 13 percent increase in the number of government requests for data, but it also shows that Facebook is still not able to be as transparent as it might want. For the first time the social network is able to report about the number of data requests that have a non-disclosure 

 Deltek estimates contractor-addressable spending on the U.S. government’s mission-critical programs will increase by $18 billion to about $682 billion in fiscal year 2017 if Congress approves the White House’s latest budget request. The report forecasts continued growth in the Federal cybersecurity, big data analytics, health care information technology and infrastructure segments despite a projected small decline in overall contractor-addressable IT spending for FY 2017. “Government demand looks particularly strong for…areas that align with the Obama administration’s focus on modernization, health care and veterans services,” said Deniece Peterson, Deltek’s director of
Deltek estimates contractor-addressable spending on the U.S. government’s mission-critical programs will increase by $18 billion to about $682 billion in fiscal year 2017 if Congress approves the White House’s latest budget request. The report forecasts continued growth in the Federal cybersecurity, big data analytics, health care information technology and infrastructure segments despite a projected small decline in overall contractor-addressable IT spending for FY 2017. “Government demand looks particularly strong for…areas that align with the Obama administration’s focus on modernization, health care and veterans services,” said Deniece Peterson, Deltek’s director of  The director of the FBI suggested Thursday that his agency paid at least $1.3 million to an undisclosed group to help hack into the encrypted iPhone used by an attacker in the mass shooting in San Bernardino, Calif.
The director of the FBI suggested Thursday that his agency paid at least $1.3 million to an undisclosed group to help hack into the encrypted iPhone used by an attacker in the mass shooting in San Bernardino, Calif. Apple says these requests typically seek information about a user’s iTunes or iCloud account, and each requires a search warrant. That information could then be used to help investigators prevent planned crimes from taking place or, after the fact, assembling a criminal case against someone. Privacy advocates are alarmed by the growing number of these
Apple says these requests typically seek information about a user’s iTunes or iCloud account, and each requires a search warrant. That information could then be used to help investigators prevent planned crimes from taking place or, after the fact, assembling a criminal case against someone. Privacy advocates are alarmed by the growing number of these  Cybersecurity is no longer the exclusive domain of corporate IT shops. In the past and in some quarters today, cybersecurity is still viewed as “some IT thing.” But the companies that take this view do so at their own peril. The specter of data breaches and denial-of service attacks are risks facing every business using
Cybersecurity is no longer the exclusive domain of corporate IT shops. In the past and in some quarters today, cybersecurity is still viewed as “some IT thing.” But the companies that take this view do so at their own peril. The specter of data breaches and denial-of service attacks are risks facing every business using  Microsoft announced last November that the company would begin offering cloud services from the United Kingdom, with the firm saying those services would extend to government organizations. Department of Defense CIO Terry Halvorsen has evangelized for the Pentagon to be more willing to allow cloud vendors to host sensitive DOD data. He would like about 50 DOD personnel to do a stint in the private sector in the coming year, and likewise bring about 50 IT hands from
Microsoft announced last November that the company would begin offering cloud services from the United Kingdom, with the firm saying those services would extend to government organizations. Department of Defense CIO Terry Halvorsen has evangelized for the Pentagon to be more willing to allow cloud vendors to host sensitive DOD data. He would like about 50 DOD personnel to do a stint in the private sector in the coming year, and likewise bring about 50 IT hands from  Data collected by the Federal government should be open and accessible to public by default, according to a group of lawmakers. According to Sen. Brian Schatz, D-Hawaii, at a discussion in Washington on Thursday, agencies these days just release data using virtual documents wherein the searcher of the information is expected to do their own digging. One of the Federal agencies that will be covered by this bill will
Data collected by the Federal government should be open and accessible to public by default, according to a group of lawmakers. According to Sen. Brian Schatz, D-Hawaii, at a discussion in Washington on Thursday, agencies these days just release data using virtual documents wherein the searcher of the information is expected to do their own digging. One of the Federal agencies that will be covered by this bill will  Microsoft wants to reveal more information on the data requests it gets from the U.S. Federal government. The company filed a lawsuit claiming the government has violated the First and Fourth Amendments by ordering Microsoft to keep thousands of data requests to the company secret. Notably and even surprisingly, 1,752 of these secrecy orders, or 68 percent of the total, contained no
Microsoft wants to reveal more information on the data requests it gets from the U.S. Federal government. The company filed a lawsuit claiming the government has violated the First and Fourth Amendments by ordering Microsoft to keep thousands of data requests to the company secret. Notably and even surprisingly, 1,752 of these secrecy orders, or 68 percent of the total, contained no  In 2010, the Obama administration’s first Federal CIO Vivek Kundra mandated that Federal agencies should try to make use of a “cloud-first” strategy instead of building more data centers. Since then, 3,125 Federal agency data centers have been closed, out of the 10,584 that existed when Kundra
In 2010, the Obama administration’s first Federal CIO Vivek Kundra mandated that Federal agencies should try to make use of a “cloud-first” strategy instead of building more data centers. Since then, 3,125 Federal agency data centers have been closed, out of the 10,584 that existed when Kundra  Sens. Richard Burr and Dianne Feinstein released the official version of their anti-encryption bill after a draft appeared online last week. The bill, titled the Compliance with Court Orders Act of 2016, would require tech firms to decrypt customers’ data at a court’s request. The Burr-Feinstein proposal has already faced heavy criticism from the tech and legislative communities and is not expected to get anywhere in the Senate. President Obama has also indicated that he will
Sens. Richard Burr and Dianne Feinstein released the official version of their anti-encryption bill after a draft appeared online last week. The bill, titled the Compliance with Court Orders Act of 2016, would require tech firms to decrypt customers’ data at a court’s request. The Burr-Feinstein proposal has already faced heavy criticism from the tech and legislative communities and is not expected to get anywhere in the Senate. President Obama has also indicated that he will  Tony Scott The White House has proposed a bill that would create a $3.1 billion revolving fund to help Federal agencies update their legacy information technology systems and bolster the government’s cybersecurity posture. He added the bill would also establish an independent board of experts to help identify agency IT systems that face the highest risk for potential cyberattacks as well as strategies to facilitate adoption of common platforms and cybersecurity best
Tony Scott The White House has proposed a bill that would create a $3.1 billion revolving fund to help Federal agencies update their legacy information technology systems and bolster the government’s cybersecurity posture. He added the bill would also establish an independent board of experts to help identify agency IT systems that face the highest risk for potential cyberattacks as well as strategies to facilitate adoption of common platforms and cybersecurity best  President Obama’s briefing means the bill will not be released this week, as Sen. Richard Burr hoped. Meanwhile, the White House on Thursday denied reports that it will not offer its
President Obama’s briefing means the bill will not be released this week, as Sen. Richard Burr hoped. Meanwhile, the White House on Thursday denied reports that it will not offer its  Will the latest White House freeze on data center expansion and construction by Federal agencies accelerate colocation and cloud deployments? In February 2011, the “Cloud First” initiative required Federal agencies to evaluate their technology sourcing strategies so that cloud computing options were fully considered. It stressed the importance of each Federal agency migrating the majority of their data to
Will the latest White House freeze on data center expansion and construction by Federal agencies accelerate colocation and cloud deployments? In February 2011, the “Cloud First” initiative required Federal agencies to evaluate their technology sourcing strategies so that cloud computing options were fully considered. It stressed the importance of each Federal agency migrating the majority of their data to  The Federal government’s Office of Personnel Management has announced plans to introduce new data breach reporting rules for health insurers that cover Federal employees, according to a Nextgov report. Director Beth Cobert argued given the breaches at OPM and other insurers and providers, the government and its partners must coordinate efforts to keep their data secure. The rules echo draft guidelines issues by the White House last August, Nextgov notes, that aim to standardize cybersecurity incident reporting among contractors that store Federal
The Federal government’s Office of Personnel Management has announced plans to introduce new data breach reporting rules for health insurers that cover Federal employees, according to a Nextgov report. Director Beth Cobert argued given the breaches at OPM and other insurers and providers, the government and its partners must coordinate efforts to keep their data secure. The rules echo draft guidelines issues by the White House last August, Nextgov notes, that aim to standardize cybersecurity incident reporting among contractors that store Federal  Combing through Federal data has typically been a daunting affair. The lofty claim is delivered about a site that aggregates Federal open data from multiple sources and displays it in interactive visuals — colorful charts, maps, profiles and even a few pieces of data-based journalism. Unlike scores of citizen analytics sites before it, Data USA embraces the role of data curator and — with minimal nudges — guides its visitors to
Combing through Federal data has typically been a daunting affair. The lofty claim is delivered about a site that aggregates Federal open data from multiple sources and displays it in interactive visuals — colorful charts, maps, profiles and even a few pieces of data-based journalism. Unlike scores of citizen analytics sites before it, Data USA embraces the role of data curator and — with minimal nudges — guides its visitors to  Ninety percent of IT professionals in the Federal government feel their organizations are vulnerable to a cybersecurity attack, according to a recent report by Vormetric. The numbers are disconcertingly high considering they come from professionals tasked with protecting the confidential information of millions of Americans as well as the classified information from certain Federal programs and policies. Despite those high numbers, nearly 60 percent of responding government IT professionals believe their network defenses are “very” effective at safeguarding data, a number the report notes is notably more optimistic than their private-sector counterparts;
Ninety percent of IT professionals in the Federal government feel their organizations are vulnerable to a cybersecurity attack, according to a recent report by Vormetric. The numbers are disconcertingly high considering they come from professionals tasked with protecting the confidential information of millions of Americans as well as the classified information from certain Federal programs and policies. Despite those high numbers, nearly 60 percent of responding government IT professionals believe their network defenses are “very” effective at safeguarding data, a number the report notes is notably more optimistic than their private-sector counterparts; 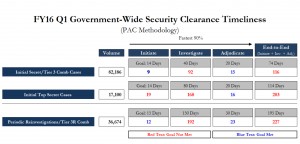
 A consortium of colleges and businesses led by the Massachusetts Institute of Technology has won a national competition to host a novel federally funded research program to turn clothing fibers and fabrics into wearable electronic devices, officials are expected to announce Friday. Clothing fibers could be designed to change color, monitor health,
A consortium of colleges and businesses led by the Massachusetts Institute of Technology has won a national competition to host a novel federally funded research program to turn clothing fibers and fabrics into wearable electronic devices, officials are expected to announce Friday. Clothing fibers could be designed to change color, monitor health, 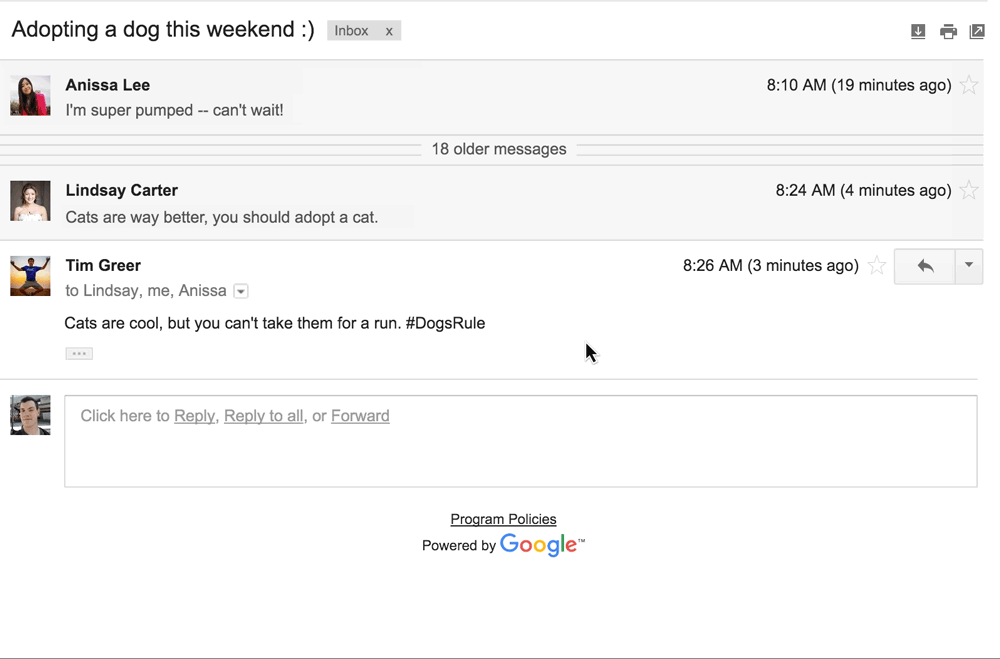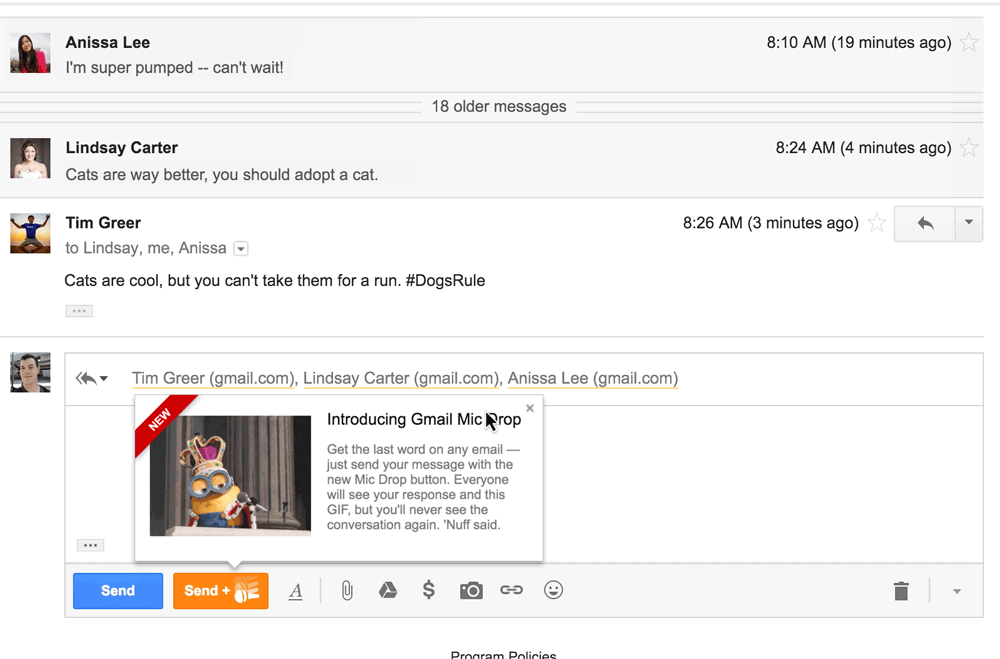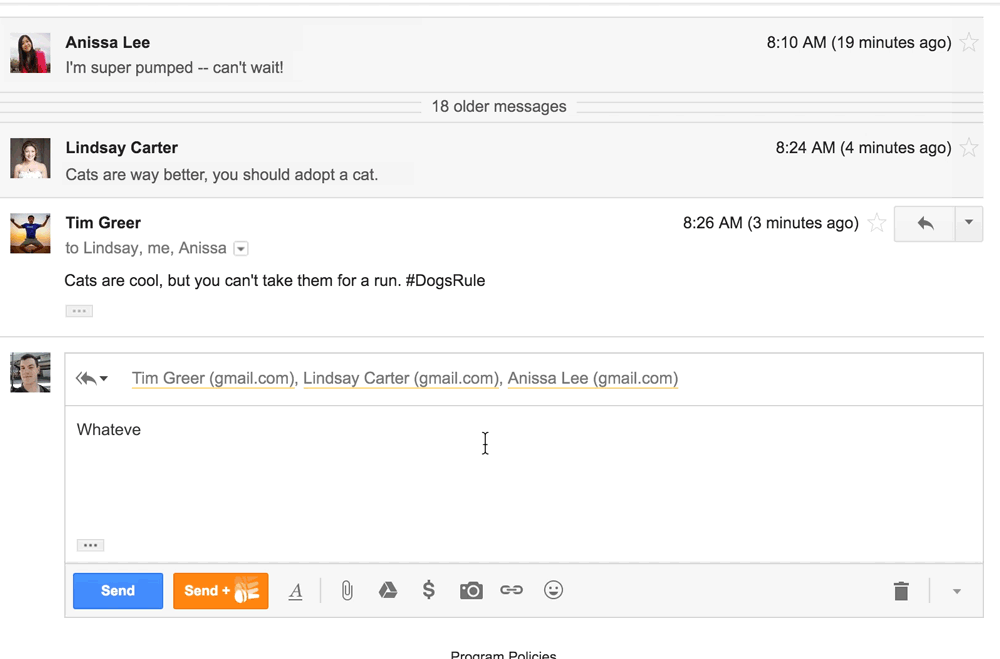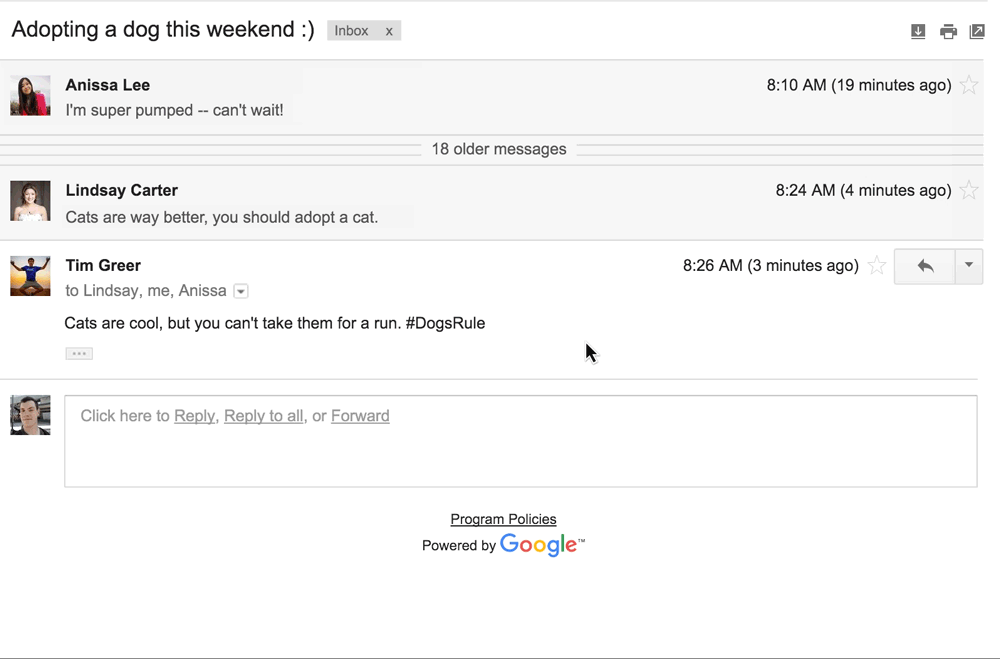 Google ended up with egg on its face after this year’s April Fools’ joke caused some Gmail users to insult contacts and, some claimed, lose employment opportunities. The “joke” was an actual feature that Google added to Gmail, called “Mic Drop.” An orange button next to the standard blue “send” button allowed people to send their email with an animated image of a Minions character dropping a microphone. Outraged Gmail users who use the service for professional purposes flooded Google’s product forums to complain about having accidentally clicked the
Google ended up with egg on its face after this year’s April Fools’ joke caused some Gmail users to insult contacts and, some claimed, lose employment opportunities. The “joke” was an actual feature that Google added to Gmail, called “Mic Drop.” An orange button next to the standard blue “send” button allowed people to send their email with an animated image of a Minions character dropping a microphone. Outraged Gmail users who use the service for professional purposes flooded Google’s product forums to complain about having accidentally clicked the  As it continues to grow, ephemeral messaging app Snapchat is receiving an increasing number of government requests for user data. On Tuesday, the Venice, Calif., company published its latest report on these requests, which it does every six months. Between July 1 and Dec. 31, 2015, Snapchat received a total of 862 criminal legal requests from U.S. government entities, up from 761 in the
As it continues to grow, ephemeral messaging app Snapchat is receiving an increasing number of government requests for user data. On Tuesday, the Venice, Calif., company published its latest report on these requests, which it does every six months. Between July 1 and Dec. 31, 2015, Snapchat received a total of 862 criminal legal requests from U.S. government entities, up from 761 in the  As social media outlets increasingly become the favorite channels for terrorist groups to spread messages of violence and recruit new members, the Internet companies that maintain those services are in a tough spot. Companies born on the Web like Google and Facebook promote an ethos of free speech, but at the same time recognize the dangers of terrorists, criminals, and other bad actors co-opting their platforms in service of a
As social media outlets increasingly become the favorite channels for terrorist groups to spread messages of violence and recruit new members, the Internet companies that maintain those services are in a tough spot. Companies born on the Web like Google and Facebook promote an ethos of free speech, but at the same time recognize the dangers of terrorists, criminals, and other bad actors co-opting their platforms in service of a  Just in time for tax season, the Government Accountability Office is warning that weak financial controls at the Internal Revenue Service leave taxpayer information at risk.
Just in time for tax season, the Government Accountability Office is warning that weak financial controls at the Internal Revenue Service leave taxpayer information at risk.

