The White House on Tuesday took a step forward in coordinating Federal response to cyber incidents in the United States with the announcement of a Presidential Policy Directive on United States Cyber Incident Coordination (PPD-41).
“This directive establishes a clear framework to coordinate the government’s response to such incidents,” Lisa O. Monaco, assistant to the president for homeland security and counterterrorism, said in her remarks at the International Conference on Cybersecurity. “It spells out which Federal agencies are responsible. And it will help answer a question heard too often from corporations and citizens alike—‘In the wake of an attack, who do I call for help?’ ”
The directive names three concurrent lines of effort, through which Federal agencies will act to respond to and mitigate the effects of cyber incidents:
- Threat response activities–Led by the Department of Justice (DOJ) through the FBI, these activities include investigating the incident, gathering intelligence, linking related incidents, identifying other affected entities and ways to pursue the threat, and facilitating information sharing with asset response.
- Asset response activities–The Department of Homeland Security (DHS), through the National Cybersecurity and Communications Integration Center, will act to provide technical assistance to those affected, identify others at risk, assess risks to that region or sector, and find ways to mitigate those risks. Some of these responsibilities will overlap with threat response, according to the directive.
- Intelligence support activities–The Office of the Director of National Intelligence, through the Cyber Threat Intelligence Integration Center, will lead this area by building threat awareness and information sharing, analyzing trends, identifying knowledge gaps, and analyzing ability to degrade threat capabilities.
In addition, if a Federal agency is affected by a cyber incident, “it shall undertake a fourth concurrent line of effort to manage the effects of the cyber incident on its operations, customers, and workforce.”
“A ‘threat response’ essentially involves investigating the crime, so that we can hunt down the bad actor,” said Secretary of Homeland Security Jeh C. Johnson in a DHS press release. ” ‘Asset response,’ like a threat response, is crucial. It involves helping the victim find the bad actor on its system, repair its system, patching the vulnerability, reducing the risks of future incidents, and preventing the incident from spreading to others.”
“PPD-41 codifies the essential role that the FBI plays in cyber incident response, recognizing its unique expertise, resources, and capabilities,” said FBI assistant director James Trainor in an FBI press release. “And as the bureau continues evolving to keep pace with the cyber threat, the authorities contained in PPD-41 will allow us to help shape the nation’s strategy for addressing nationally significant cyber incidents.”
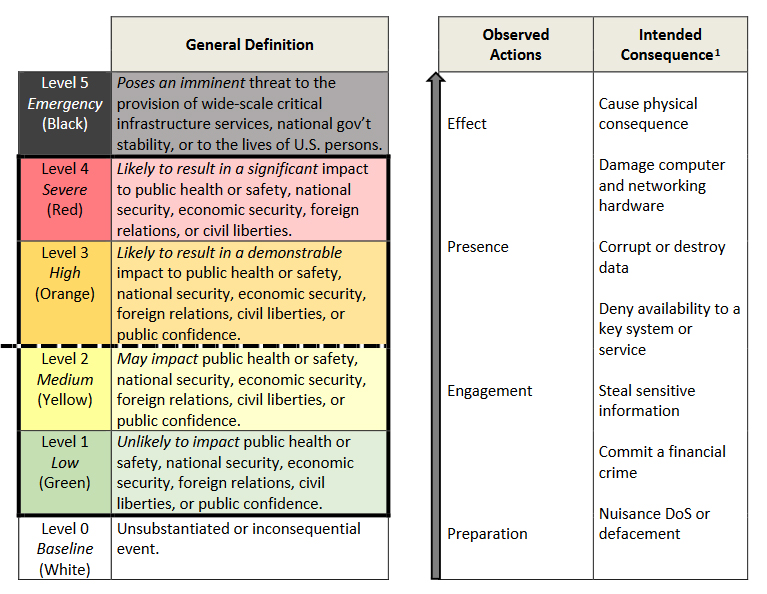
In conjunction with this directive, the White House also released a cyber incident severity schema, which establishes a common framework through which Federal agencies can evaluate cyber incidents.
The establishment of the FBI as the lead in Federal response to threats is significant, as a hearing on small business cybersecurity earlier this month revealed that many businesses do not know who to go to as the first response to cyber incidents. To this end, the directive requires that DOJ and DHS maintain a record of government contact information for the public to use in the event of a cyber incident.
Communication is a core aspect of the new directive, as it emphasized the need to coordinate with state, local, tribal, and territorial governments as well as international partners. The directive also codifies the establishment of a Cyber Unified Coordination Group (UCG), which will act to coordinate Federal agencies and, when necessary, private-sector partners in the event of a cyber incident.
“A Cyber UCG shall be formed at the direction of the NSC Principals Committee, Deputies Committee, or the CRG [Cyber Response Group], or when two or more Federal agencies that generally participate in the CRG, including relevant SSAs, request its formation,” the directive says. “A Cyber UCG shall also be formed when a significant cyber incident affects critical infrastructure owners and operators identified by the Secretary of Homeland Security.”
This directive builds on the goals set forth in the Cybersecurity National Action Plan (CNAP), released by the White House in February.
“We’re not going to wait for the next attack to hone these new procedures and capabilities,” said Monaco. “Over the next few months, agencies will be incorporating the new guidance into exercises like Cyber Guard and Cyber Storm—the nation’s largest cyber exercises. These will be done in partnership with a wide array of industry organizations and agencies like the Departments of Energy and Treasury. And next week we will bring together industry and government experts to lay out this new policy and get vital industry feedback on how best to implement it.”